
Background information
Are those the new Microsoft Office logos?
by Michelle Brändle

In May, a hacker group called Storm-0558 accessed e-mails as well as other data from US government agencies. This went unnoticed for a long time and the implications were underestimated. This was apparently due in no small part to Microsoft.
In mid-July, it became known that a suspected Chinese hacking group called Storm-0558 had launched a cyber attack. This resulted in hackers accessing e-mails in 25 different accounts belonging to US government agencies. However, this wasn’t a one-time access breach. Hackers had access to electronic correspondence for about a month. The start time of the hack – in May – is considered to be particularly critical. That’s when US Secretary of State, Tony Blinken, met with Chinese government officials in China to negotiate important business deals.
The origin of the Storm-0558 hack is believed to stem back to a weakness in Microsoft’s Outlook Web Access (OWA) and Outlook.com. The hacker collective managed to forge an authentication token to gain access. This allowed them to impersonate Azure Active Directory (AAD) users, get through the validation process and into e-mail accounts. It shouldn’t really work like that. According to Microsoft’s service description, this authentication method should only be possible for personal, not business accounts in AAD. Microsoft can’t (or doesn’t want to) explain how this was able to happen.

The Cybersecurity & Infrastructure Security Agency (CISA) is also on pacifying manoeuvres for the time being. The contents of the e-mails affected were harmless. Microsoft also assumed it was an espionage attempt rather than sabotage. However, this was hardly successful.
However, this cyber attack now brings questions and problems to light that are much more far-reaching and don’t just relate to this hack. The first question is why the extent of the hack only became evident so late – namely the week before last, a good month after hackers first gained access.
The breach was only discovered after a thorough study of detailed log protocols by a US authority. You need a subscription called Microsoft Purview Audit (premium) to view these. This is a tool that logs everything that happens in a system in great detail. It costs extra and isn’t included as part of Microsoft’s standard package. If a customer doesn’t want (or can’t afford) this, they’ll be in the dark about it. In short, customers without this subscription wouldn’t have been aware of this data breach.
It’s not just experts who’ve been voicing their criticism; politicians have also joined the outcry. And not without reason. According to a CISA press release, the US government is about to embark on a cloud-based cybersecurity strategy. Incidents like these have torpedoed the plans. As Microsoft has now announced, Purview Audit (premium) will be included in the security package free of charge in future.
As it now turns out, the incident could have much further-reaching consequences than initially thought. Security company Wiz claims to have identified the Microsoft key the hackers used to snoop on e-mails. This is done using lists of valid signature keys, which are publicly available.
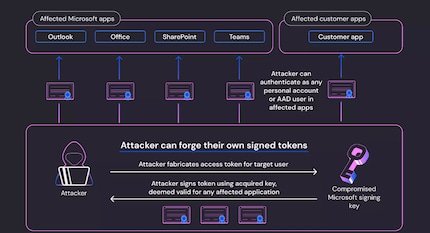
The stolen key wasn’t a copied token. It was actually an OpenID signing key for AAD. Think of it as a kind of master key to Microsoft’s cloud system.
Wiz explains that, according to their findings, the attackers didn’t just have potential access to Exchange Online, hosted by Microsoft, but in fact, to almost all areas of Microsoft’s cloud. In other words, to Office, Teams, Sharepoint and Outlook. But that’s apparently not even all of it. As Wiz goes on to explain, the stolen key could sign any OpenID access token. This in turn would mean that the hackers could theoretically gain access to any cloud app that used Azure Active Directory as its identity validation, irrelevant of the company. It was reported that accounts offering logins with Microsoft would also be affected, such as GitHub.
Microsoft has now blocked the key, meaning hackers shouldn’t have any further access. However, we can’t rule out the idea that the hackers built a backdoor into previously compromised accounts so they no longer need this key.
Microsoft is yet to confirm the situation described by Wiz. While I have little doubt about Wiz’s assessment, it still remains to be seen whether hackers did indeed exploit these possibilities, and if so, to what extent. To know for sure, we’d first need a review of all Microsoft accounts, including those based on AAD. But how would that work? Either way, the story is a fiasco of epic proportions for Microsoft. What’s more, its strategy of non-communication or barely communicating at all isn’t transparent and, in my opinion, not appropriate. The damage has already been done, so now the company needs to learn some lessons from it. Otherwise, this will erode more trust in Microsoft than before.
Header image: Shutterstock
I've been tinkering with digital networks ever since I found out how to activate both telephone channels on the ISDN card for greater bandwidth. As for the analogue variety, I've been doing that since I learned to talk. Though Winterthur is my adoptive home city, my heart still bleeds red and blue.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all