
Background information
Tracing back the digitec phishing e-mails
by Dominik Bärlocher

The e-mail containing malicious script recently sent by phishers has now been analysed. Read on to find out how it works and how to get rid of the pest.
After receiving reports of circulating phishing e-mails using digitec as the sender, we warned our users and set out on a mission to get to the bottom of the attack.
While others enjoyed a relaxing weekend curled up on their sofas, the team lead by Christian Margadant, Head of Technics at Digitec Galaxus AG, decoded and analysed the malicious code. “We can almost certainly say what exactly the malicious code wants to do to computers”, he says.
Margadant carried out the analysis with utmost caution – accidentally running the code could have had severe consequences for the entire Digitec Galaxus AG network. When starting an analysis, you’ve got to be prepared for the worst: deleted data, encrypted files and more. “I looked at the code on a laptop that wasn’t connected to the Internet or the network”, he explains. Furthermore, the laptop contained no personal data that would have been missed should things have gone wrong – so pretty much the opposite of computers used by our customers. “At worst, I would have re-set the laptop and solved the malware problem that way.”
However, he did not use the isolated laptop for long. He soon realised that the computer would be safe as long as he was decoding the code in a safe and isolated context. He did not use any special tools: “Firefox, Developer Console and some websites. Basically that’s it. The important thing when examining a malicious code is to save it in a file that cannot be accidentally executed. In other words, not as a JavaScript file but as a normal text file.”
The malicious code contained in the e-mails follows a simple pattern. A word file is used as a launch platform for the code before the latter starts carrying out complex functions. Although the more complex part is encoded, it’s easy to decipher. “Somewhere in the code, there is a function that transfers all used characters to the decryption”, says Margadant, “as soon as it has been found, it can be used against the malware to decipher the code.”
Margadant is lucky in the first stage of decoding. Not only does he come across further encrypted blocks but also finds clear text parts that he can read. What’s more: “The code is well-commented so I can just read what the uncoded part is up to.” This points towards the work of amateurs as the comments make it easy for so-called Script Kiddies (someone using ready-made software) to compile and modify codes themselves. However, the other encoded parts look a lot more professional.
So now that the code has been cracked, we can tell you what the Malware actually does.
The good news: Your data has neither been deleted nor encoded. The bad news: Your money is no longer safe. But first things first.
As a first step, the malware prepares the ground for more complex operations.
Although this in itself is not harmful, it does provide fertile ground for more malware. Particularly the certificates play an important role in the further course of the operations.
The second step involves performing downloads. None of the downloaded programmes are malware or evil per se. On the contrary. In certain parts of the world, they are part of digital survival.
Next, the malware starts TorBrowser and Proxifier. To ensure they keep running in the background, they are called as a Scheduled Task. These background processes are disguised.
This is where it first becomes apparent what the software is actually doing. The Proxifier is given a profile that forwards requests to certain websites via a route that is controlled by third parties. These are as follows:
We can conclude from the banks listed that the attack was only aimed at bank customers in Switzerland and Austria. In other words, the attackers know precisely who they’re targeting. This script was probably only spread throughout Switzerland and Austria as it would have no effect on bank customers in other countries. Bank customers in Switzerland and Austria, however, are affected as follows: When you access your e-banking system, the traffic is "eavesdropped" on. So what we're dealing with is a standard man-in-the-middle attack.
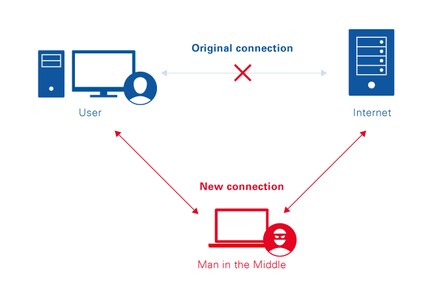
A man-in-the-middle attack is an attack that forwards the user’s traffic to a host via a third party. There it is “eavesdropped” on.
As Christian Margadant and his team cannot access the pages on the Dark Net, the Head of Technics sees one of two possibilities:
The easiest and by far the most thorough solution to rid your system of the malware is to completely re-install Windows. This was also correctly suggested by the user Deville_TGR in our previous article.
So, just re-install your OS?
Yep. Although it’s not always possible let alone desired, it is recommended. In the event that you can’t or won’t re-install Windows, the following advice applies alongside the first piece of advice mentioned in the first article.
This method curbs the threat but leaves its traces.
Christian Margadant ran the script under controlled conditions. He can now safely say that this was a man-in-the-middle attack. Furthermore, the script is identical to a file originating from a sender claiming to be SBB even though it was actually sent by sbbclient@sbb.rs.
Windows 10 users are lucky. The definitions in Windows Defender v1.231.1459.0 timestamped 08.11.2016/20:24 show that Microsoft’s latest operating system recognises the JavaScript file that wants to run malicious code and stops it in its tracks. Furthermore, no registry entries are made and certificates are only installed after the user confirms.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all