
Background information
What the digitec phishers are really after
by Dominik Bärlocher

Currently, fraudulent e-mails containing payment requests for a digitec article are in circulation. These e-mails are fake and originate from an unknown sender. We’re on a quest to investigate this matter. Who are the hackers behind these phishing e-mails? And please do not open any attachments in dodgy-looking e-mails.
Red alert for our customer service. Several customers reported having received blatantly fake e-mails from us. The e-mails request payment for an order that is not further mentioned.
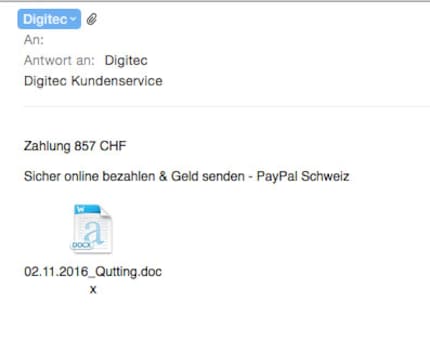
The e-mail is short and sweet.
We’re not exactly spoilt for clues when it comes to tracking down the culprits. However, one thing that can be concluded from the e-mails is that the people behind the attack do not speak German. If they did, surely they would have made the effort to add a short text. But they didn’t. All they did was attach a payment slip and a Word document in the format “.docx”.
The e-mail shows sender adresses such as Digitec@ropa-maschinenbau.de, a company that manufactures large machines. It probably goes without saying that we do not have an address at Ropa. Furthermore, it can be assumed that the hackers are not sat at the Ropa office but are taking advantage of a weak spot in the company’s e-mail system. Another possibility is that the e-mails were configured to show a different sender.
This enables e-mails to be sent from numerous addresses from companies that have no interest in damaging you in any way. What is very interesting though are reports of e-mails being sent from the domain digitec.com. This domain does not belong to us but to someone else.
Our research has revealed that the digitec.com domain belongs to the Digitec Corporation in Yonkers, New York. Further research has shown that the Digitec Corporation really exists.
The Digitec Corporation on a map
We can, however, conclude that these criminals – provided they are the owners of the domain – got their hands on Digitec.com a while ago as it remains in their possession until June 2019. In other words: They either bought the domain five months or two years and five months ago.
However, there is an indication that the Digitec Corporation is not behind these e-mails. The e-mail address registered for the domain is digitec@compuserve.com – compuserve being a free e-mail service provided by the Internet giant AOL.
The payload, that’s the part of the attack that harms your PC, is hidden in the e-mail attachment. The attachment is a docx file. A file that can be opened with Microsoft Word. This is what it looks like after opening.

The opened attachment
The attachment is written in terrible German and can roughly be translated as follows:
This is detailment your account
To see receipt, click twice on image.
The broken German provides a further clue that the attackers have no command of the language. Most elementary school kids would have done a better job.
WARNING: Don't go near attachments from unknown sources. Opening the files alone can be dangerous. We assume no liability for any damage caused to your computer.
In PCs with default Windows settings, double-clicking on the image triggers a JavaScript that runs further code.
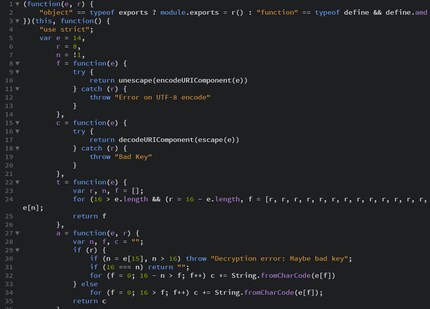
The beginning of the payload code
An IT security pro took a quick look at it. His guess: “Looks like code compiled into JavaScript.” The attackers were smart. They encrypted the code written as JavaScript in another language and put it into code that is understandable by any machine. The decryption can also be read and carried out by machines.

Excerpt from an encrypted part of the payload
What it is that the programme does is hard to say with the time and means available at the moment. The expert’s estimation: “It will most probably download further malware.” Both our in-house and external experts are analyzing the situation and looking for further clues in the code.
Security is one of our prime concerns. Therefore, we are currently unable to provide you with further information. It’s not that we don’t want to tell you but that an attacker can use the information against you or us.
As the current case proves: We are a target. And we want to give the attackers as little means and information as possible. The current case also proves that, although the attackers know who we are, they don’t know us well enough. Help us by giving no foothold to these blatant fakes!
A bit of practical information for you: We always send invoices in PDF format. No matter what kind of digitec invoice you may receive – if it’s not in PDF format, it’s not from us.
With this in mind, stay safe and refrain from opening e-mails that are in any way suspicious – even if they look like they’re from digitec or Galaxus. The only domains we use for sending e-mails are @digitec.ch, @digitecgalaxus.ch and @galaxus.ch.
If you accidentally double-clicked on the image, all is not lost. Our internal IT department has decoded the e-mail’s code and exposed the purpose of the malware.
It modifies your computer or rather your browser in a way that allows it to visit .onion websites without the generally required proxy. These websites can be found in the so-called Dark Net. Furthermore, the attachment installs a certificate that allows your computer to access certain sites that are otherwise not accessible to the public. We currently do not know what exactly happens on these sites. It’s quite possible that this is where further software is obtained. According to our IT department, it is also possible that these sites are used as control pages for botnets or the like. With the connection to the .onion site, it’s theoretically possible to give your computer commands.
If you want to beat the infection, try the following steps:
Although this does not undo all changes the malware has made to your computer, it does interrupt the communication channel to the Dark Net. According to our current state of knowledge, it also renders it harmless, even if some data remains on the PC. We are currently working on creating a manual on how to fully remove the malware.
Christian Margadant and his team have fully decoded the malicious code. We now know exactly what the phishers want, how they proceed and how you can rid yourself of the malicious script.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all