
Background information
7 questions and 7 answers on the Meta trial
by Samuel Buchmann

Researchers have found that Meta and Yanex are able to decipher their user’s details. In just one move, they illegally obtain sensitive personal information about millions of Android users. What does that mean for us?
For years, tracking pixels have been a vital tool for advertisers on the internet. Social media services such as the Meta Group also collect data to measure the effectiveness of ads and analyse user behaviour. Meta and the Dutch-Russian service Yandex have now gone one step further. Until now, «pseudonyms» were used for tracking. In other words, a user disclosed their behaviour on the web, but no concrete conclusions could be drawn about their identity.
But Meta and Yandex have found a way to almost completely de-anonymise their users. This affects users of Android devices whose browsers have been technically manipulated to provide information for the companies’ apps, such as Facebook, Instagram or Yandex apps.
Researchers from Spain and the Netherlands found that both corporations were using a technology that delved deep into the connection of browsers and apps on Android devices. Yandex has already been using this trick since 2017, whereas Meta began using it in September 2024.
At the centre of it all are tracking pixels – small invisible scripts that are embedded on websites. These were manipulated by the two companies in such a way that they were able to access much more sensitive information via the apps installed on devices.
The foundation for the offensive lies in one of Android’s functions that few people are familiar with. Apps in the background can receive data using local host addresses – i.e. on communication channels that are actually only used internally on the device. These aren’t automatically blocked by security checks, so they don’t require any special authorisation from the device.
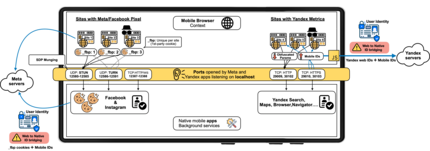
The apps took advantage of this. As soon as a user accesses a website that contains the Meta Pixel or Yandex Metrica, a data packet is sent via this local connection. The app, even if it’s running in the background, recognises this request, reads the identifier it contains and compares it with the logged-in user account – for example, the Facebook account. An anonymous web session suddenly becomes a personal data record, linked to a real name, a user profile – and an entire digital history. This also works when you’re in incognito mode.
According to the researchers, almost six million websites are equipped with the Meta Pixel and a further three million use Yandex Metrica. These include retailers and telecommunications companies in Europe. You can find out exactly which websites are affected on the research team’s GitHub page. An analysis by the researchers revealed that over 70 per cent of these sites didn’t ask their users for consent to this tracking – which is legally mandatory due to GDPR. Many website operators were also unaware that the trackers were establishing connections to local ports on the end devices. And those who noticed were ignored by Meta.
Immediately after the study was published, Meta and Yandex discontinued this strategy. Meta announced that it was in talks with Google to clarify «misunderstandings» regarding the platform guidelines. Yandex announced that it would disable it – but emphasised that it hadn’t collected any sensitive data.

The browser developers are now reacting to the research findings. In a new version of Chrome, Google blocked certain variants of SDP Mungings – i.e. the technology that established these connections without authorisation. Browsers such as Brave and DuckDuckGo also rely on comprehensive blocklists to prevent data from being sent to local ports. Mozilla, the manufacturer of Firefox, is examining the technology and has announced investigations. It’s still unclear how things will proceed legally for Meta and Yandex.
However, the researchers have said that you shouldn’t get your hopes up. If Meta and co. change the port – until now it’s always been port 12387 – or use a different protocol, this technology could still be used. It’s down to Android to provide a permanent solution.
The most effective protection against this type of tracking currently is to remove the Meta and Yandex apps from your Android device and use the services via the browser, if at all.
Alternatively, it helps to use browsers that block trackers or prevent connections to local ports by default (Brave or DuckDuckGo Browser). You’re apparently safe if you use an iPhone: up to now, iOS hasn’t allowed this kind of background technology to the same extent.
I've been tinkering with digital networks ever since I found out how to activate both telephone channels on the ISDN card for greater bandwidth. As for the analogue variety, I've been doing that since I learned to talk. Though Winterthur is my adoptive home city, my heart still bleeds red and blue.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all