Security flaw in macOS High Sierra: All you need to know about Apple’s bug and how to protect your Mac
A security flaw has been discovered in Apple’s macOS High Sierra operating system. But not just any flaw; this one is really bad and extremely easy to exploit. I’ve tested it and have summarised all you need to know – including how to protect your Mac.
Apple’s hardware is good. Apple’s software is good. Everything Apple does is no less than good. This also applies to the security flaws in their system. The one that was discovered yesterday is not just a bug, it’s a good one. And by good, I mean major.
To verify the news, I grabbed a Macbook from one of our designers and tried it out. The result: Yes, it’s a security flaw and yes, it’s really bad.
Username root, no password
Exploiting this security gap is easy. Remember the window that asks you to re-enter your password to access resources? You’ll find it in the system preferences. It’s the one that pops up when you’re changing settings and asks you to enter the username and password for your account. In my case, the username is «Creation» and the password is a well-kept secret.
Creation might not have access to resources. This happens often in companies where the internal IT department handles all devices and some system preferences can’t be adjusted by individual employees. In this case, you can only get access if you have the administrator password.
When this window appears, enter the following user name:
rootLeave the password empty and press enter. If it doesn’t work at first, just repeat pressing enter and it will work eventually. When we tested it at the office, we never needed more than two attempts.
That’s it, you now have access to the resources and you can change any system preferences as you wish. Lemi Orhan Ergin, a Turkish Information Security Researcher, discovered this flaw yesterday and took to twitter to share his findings.
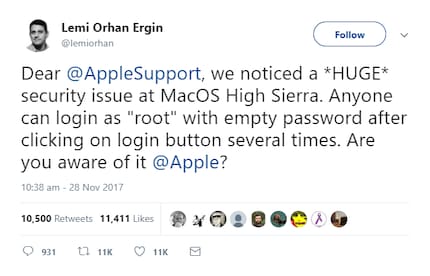
This is worrying.
How to prevent unauthorised access to your Mac
The good news for users is that you can fix this security gap just as easily as you can exploit it. Just change the root password. To do so, you need to activate the root user, as this user is deactivated by default.
- Go to the Apple menu
- Choose System Preferences
- Click Users & Groups (or Accounts)
- Click the padlock symbol on the bottom left
- Enter your name and password or the root hack described above
- Click Login Options
- Click Join (or Edit)
- Click Open Directory Utility
- Click the padlock symbol in the Directory Utility window and enter your password or the root hack
- From the menu bar: Choose Edit > Enable Root User
- Enter the password that you want to use for the root user
If you’re looking for a shorter solution, open a terminal and enter this command line:
sudo passwd -u rootIsn’t it ironic that you can prevent a hack with a hack? Just saying.
Apple will probably release a software update to address this issue within no time. The solution is rather simple: The structure and implementation of the root user can’t be changed, but Apple can disallow empty password fields.
What have we learned? Next time Apple asks you to install an update, do it.
Who or what is root? My Mac doesn’t have it
The root user is one of the default accounts on Unix-based systems. Apple’s macOS is Unix-based. It’s not surprising that an account which is called «root» is extremely important. In fact, it’s the most important account in the system.
root is the system’s administrator account. It can’t be removed.
This account has all rights on the computer or network, making it an extremely powerful tool. The equivalent user on Windows is called «Administrator».
Well, that’s it. All that’s left to say is change the password of your root account and install the update as soon as it’s available. Stay safe!
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all