
MS Office zero-day vulnerability: "Follina" puts millions of Windows users at risk
A vulnerability that has not yet been patched means that users of Microsoft Windows can catch malware. Microsoft itself has published instructions on how to prevent this.
The zero-day vulnerability is called "Follina" and affects Microsoft Office in combination with the Microsoft Diagnostics Tool (MSDT). All supported versions of Windows are affected. According to a report by Ars Technica, it has been exploited for over seven weeks. It can be abused via specially crafted Office documents. The perfidious thing about it is that the hover preview of a downloaded file should be enough to hover preview is enough to infect the system.
Microsoft has already confirmed the vulnerability and describes it as follows: "A remote code execution vulnerability exists when MSDT is invoked via the URL protocol from an invoked application such as Word. An attacker who successfully exploited this vulnerability could execute arbitrary code with the privileges of the calling application. The attacker can then install programs, view, modify or delete data, or create new accounts in the context allowed by the user's privileges."
There is no patch from Microsoft yet, but the company has released a temporary workaround that disables the MSDT URL protocol. This will prevent corresponding links from being called. Microsoft recommends the workaround until a fix is released via update.
How to disable the MSDT URL protocol
This is how Microsoft's workaround works:
1.
Start the command prompt as administrator. You do this by pressing the Windows key, then typing "cmd", right-clicking on the application and selecting "Run as administrator".
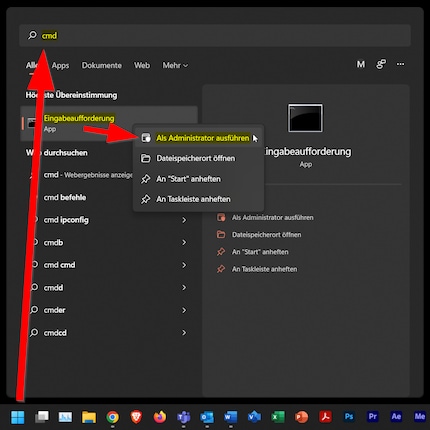
After that you have to confirm with "Yes".
2.
Now first make a backup of the registry key by typing the following and confirming with Enter: "reg export HKEY_CLASSES_ROOT\ms-msdt filename".
You can of course replace the "filename" at the end with another filename of your choice. The backup will be created in this form in the directory where you are.
After that you deactivate the log with the following command and the enter key: "reg delete HKEY_CLASSES_ROOT\ms-msdt /f".
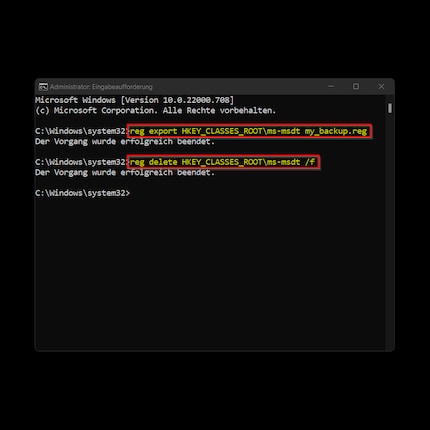
This does the job. If you want to undo the deactivation, start the command prompt again as administrator and enter the following: "reg import filename". This will restore the backup you created.
I find my muse in everything. When I don’t, I draw inspiration from daydreaming. After all, if you dream, you don’t sleep through life.
From the latest iPhone to the return of 80s fashion. The editorial team will help you make sense of it all.
Show all