
Mac malware steals browser data and crypto assets - also in the future
A security researcher discovers new malware on the internet. It targets personal data and crypto assets and is ready for the future. It is also said to work on macOS 14 "Sonoma". However, the operating system will not be released until October.
A security researcher who calls himself "iamdeadlyz" online has discovered a new malware. He has christened it "Realst". This is currently being used very actively on Macs. Interestingly, the latest variant of the virus is already operational under macOS 14 "Sonoma". This is despite the fact that the operating system will not be released until autumn.
The malware finds its way onto your computer via fake blockchain games. The games are actively advertised on various websites, social media platforms and on Discord. Some of them are already known by name:
- Brawl Earth WildWorld
- Dawnland
- Destruction
- Evolion
- Pearl
- Olympus of Reptiles
- SaintLegend
Interested parties will then be sent an access code by personal message. This code is required to download the alleged games from the websites of the "manufacturers". Sometimes it is also claimed that beta testers are being sought. Despite this somewhat clumsy strategy, the perpetrators appear to be enjoying increasing success.
The installation packages do not contain games, however, but the corresponding malware. Specifically, it is a ".pkg" or a ".dmg" file. These in turn contain two files with the names "game.py" and "installer.py".
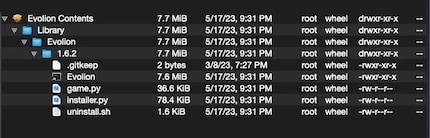
Source: SentinelOne
"game.py" is a Firefox stealer, "installer.py" is a so-called "chainbreaker". The name of the Firefox stealer says it all. It bypasses the encryption of the Mozilla browser and accesses any stored passwords, credit card numbers and other data. Chainbreaker is an extractor programme that can read the macOS keychain. Passwords, keys and even certificates can be misused in this way.
If files are provided with certificates, the operating system classifies them as trustworthy. As the experts have discovered, this has happened several times in the past. Even signatures from Apple developer IDs were used. These have since been deactivated.
"Realst" appears in various forms
As SentinelOne further discovered, there are 16 variants of "Realst", which are structured differently. The procedure is also different. What they all have in common, however, is their goal: to siphon data from browsers (Firefox, Chrome, Opera, Brave and Vivaldi), the Telegram desktop app and various crypto wallets.
Caution is therefore advised when downloading blockchain games. If such an incident has already occurred, it helps to reset the device. Saved passwords and other sensitive data should also be changed as quickly as possible.
Cover image:Shutterstock
I've been tinkering with digital networks ever since I found out how to activate both telephone channels on the ISDN card for greater bandwidth. As for the analogue variety, I've been doing that since I learned to talk. Though Winterthur is my adoptive home city, my heart still bleeds red and blue.
From the latest iPhone to the return of 80s fashion. The editorial team will help you make sense of it all.
Show all