
How smart speakers can be hacked through the window
Researchers have uncovered a new smart speaker vulnerability: Smart speakers can even be hacked remotely using a laser. According to experts, the only remedy is to redesign the microphones.
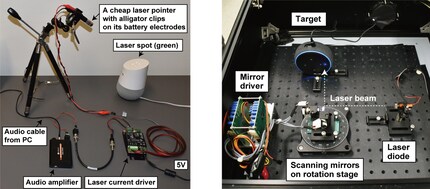
Do you think your smart speaker is protected from unauthorised access within your own four walls? Well, I'm afraid I have to disappoint you: Researchers from Tokyo and Michigan have presented a scientific paper according to which they have succeeded in hacking smart speakers with laser pointers. With the help of a few additional, commercially available gadgets - a laser diode driver and an audio amplifier - the researchers were able to ask other people's speakers about the weather, order goods on the internet and open garage doors, doors and cars.
Inconspicuous and from a distance
In addition to the well-known smart speakers from Alexa and Google, the experts also gained access to an iPhone XR, a 6th generation iPad, a Samsung Galaxy S9, an Amazon Fire Cube TV and a Google Pixel 2. As voice-controlled systems often work without user authentication, the experiment was successful without cracking the password or PIN code. Even with protected systems, a brute force attack was sufficient, as there was no numerical limit to the password or PIN entry.
The beam of a commercially available laser pointer managed to outwit the systems. A PC, a laser diode driver, an audio amplifier and a few cables were enough to open foreign doors and locks without any problems. The researchers were able to gain access to other people's smart speakers from a distance of up to 110 metres and give them commands using laser beams. One prerequisite for this is, of course, that the device to be hacked is in the field of vision of the offender.
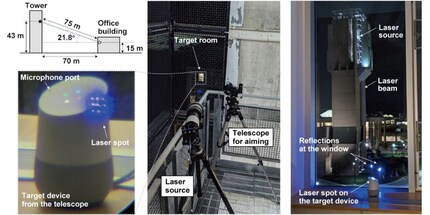
Another limitation of this hack is that the laser must be aimed precisely at a specific part of the microphone in order to gain access. However, with a little practice, even an occasional thief can manage this. In addition, the laser beam or its reflection can be perceived by other people - especially if the attack takes place in the dark. Unless the hacker uses an infrared laser. Finally, entered commands are usually confirmed with a voice response from the smart speaker, which would also alert people in the vicinity.
The diaphragm makes it possible
The laser attacks exploit a vulnerability in the microphones of smart speakers. All microphones based on a microelectromechanical system (MEMS) are vulnerable. The microscopically small components of these microphones respond to light as if it were sound waves. Although the researchers have only tested Siri, Alexa, Google Assistant, Facebook Portal and some mobile phones, they fear that all devices that use MEMS microphones are at risk.
Because such microphones convert both sound and light into electrical signals, lasers can transmit direct commands to smart speakers. So if a hacker uses some gadgets to convert an electrical signal into a certain intensity of a laser beam, they can fool the microphone and trick it into giving a voice command. How is this possible? A small plate in the microphone - also known as a diaphragm - begins to move when sound is detected and transmits the commands in the form of electrical waves to the control centre of the intelligent loudspeaker. Laser beams can imitate this movement and fool the diaphragm in this way.
Quo vadis, MEMS microphone?
Although there are some limitations and further devices are needed, the findings of this study are highly alarming. Not only does the study show another vulnerability of smart speakers and voice-controlled devices in general, but also that these attacks are possible in realistic everyday situations. The fact that the researchers are not yet able to fully understand all the processes behind the hack is also dangerous. Last but not least, the results show that password- and PIN-protected devices are more necessary than ever.
What needs to be done to protect MEMS microphones from such laser attacks? A simple adhesive tape over the microphones as a quick fix is not enough, as stronger light sources penetrate the adhesive tape. Some researchers from Japan and the USA are talking about a complete redesign of the microphones. This is a complex process and does not happen overnight.
When I'm not stuffing my face with sweets, you'll catch me running around in the gym hall. I’m a passionate floorball player and coach. On rainy days, I tinker with my homebuilt PCs, robots or other gadgets. Music is always my trusted companion. I also enjoy tackling hilly terrain on my road bike and criss-crossing the country on my cross-country skis.
From the latest iPhone to the return of 80s fashion. The editorial team will help you make sense of it all.
Show all