
Cyber attack on Matisa: Grief hacker group strikes again in Switzerland
After the comparison service Comparis was attacked by the hacker group Grief, another Swiss company is now being blackmailed via ransomware. The culprits penetrated the systems of Matisa, a track construction company headquartered in Crissier (VD).
Anyone who visits the website of the track construction company Matisa Matérial Industriel S.A. right now is greeted by a note in which the company informs about the ransomware attack on their systems that took place on 20 July 2021. As the company states, it has blocked some IT systems for security reasons and deeply regrets the inconvenience caused by this incident.
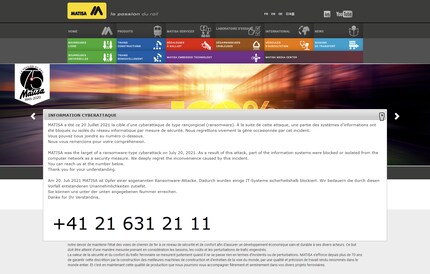
Matisa is currently at the same point the Swiss comparison service Comparis was on 7 July when they were the target of a ransomware cyber attack by the same hackers. Who are the hackers? The group Grief, who always follows the same pattern and uses aggressive blackmailing tactics. The bottom line is this: pay or suffer.
The group, who’s only been active since spring this year, seems to not only compromise victims' systems with appropriate ransomware and encrypt their data, the hackers also pull a backup of everything they can find. And then they do what they once announced themselves in an earlier statement on the darknet:
Now we define the rules of the game, fuck discounts, fuck negotiations, fuck time wasting… Pay or Grief. This is our statement.
What this means is that Grief won’t wait around. If victims don’t pay a ransom, they may not be able to decrypt the encrypted data. On top of this and even worse, Grief announces to start releasing i.e. publishing the stolen data after a week at the latest.
If you visit Grief's darknet website, you'll find a list that neatly details most of their past attacks – as well as the current operations or blackmailings that are still in progress and the most recently completed ones.
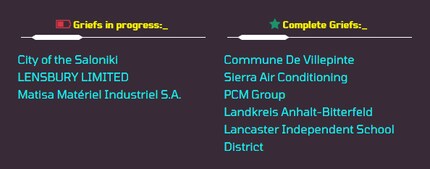
As you can see on the screenshot, Matisa is their third last victim. Since then, Grief has also targeted the second-largest city in Greece and a hotel in London. The status «In Progress» indicates that the blackmailing operations aren’t finished yet.
The current list of previous Grief actions includes 25 entries. Strangely enough, there’s currently no entry for Comparis. Was Grief not thorough when they listed their targets or are there other reasons for this? We can only speculate about this right now.
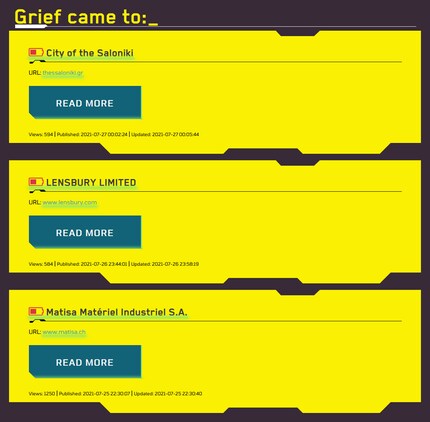
Clicking on the details page of Matisa reveals the URL of the hacked company website and a short info text about the company, which also mentions the number of employees and the turnover. On top of this, there are examples of the stolen data. More specifically, two screenshots are shown: a checklist and an internal Excel calendar spreadsheet. And then there’s a downloadable 773-kilobyte file called «Audit Schedule 2021.zip».
We don’t know whether Matisa has paid a ransom or will do so. However, it’s not advisable. Nevertheless, at least according to the hackers, there are also arguments in favour of paying it. That’s clearly stated on the following banner, which Grief has placed prominently on their darknet website:
Here’s the brazen banner in large.
I find my muse in everything. When I don’t, I draw inspiration from daydreaming. After all, if you dream, you don’t sleep through life.
From the latest iPhone to the return of 80s fashion. The editorial team will help you make sense of it all.
Show all